Botnet Marketplace Statistics in 2021

Botnet markets have been evolving and growing since they first emerged in 2018. These automated stores sell stolen login credentials for websites and platforms, obtained from computers infected with an infostealer, to cyber criminals. Some markets provide a full system of fingerprints to threat actors so they can mask themselves as victims.
Cognyte’s latest annual report explores botnet markets on a macro level by examining the top four markets: Genesis, Russian Market, 2easy and Amigos. Our research included the investigation of over 9 million stolen login credentials collected between 2019 and 2021. The number of login credentials sold on these markets is increasing, with the number of stolen credentials in 2021 numbering over 3.8 million, as compared to 5.2 million sold in 2019 and 2020 combined.
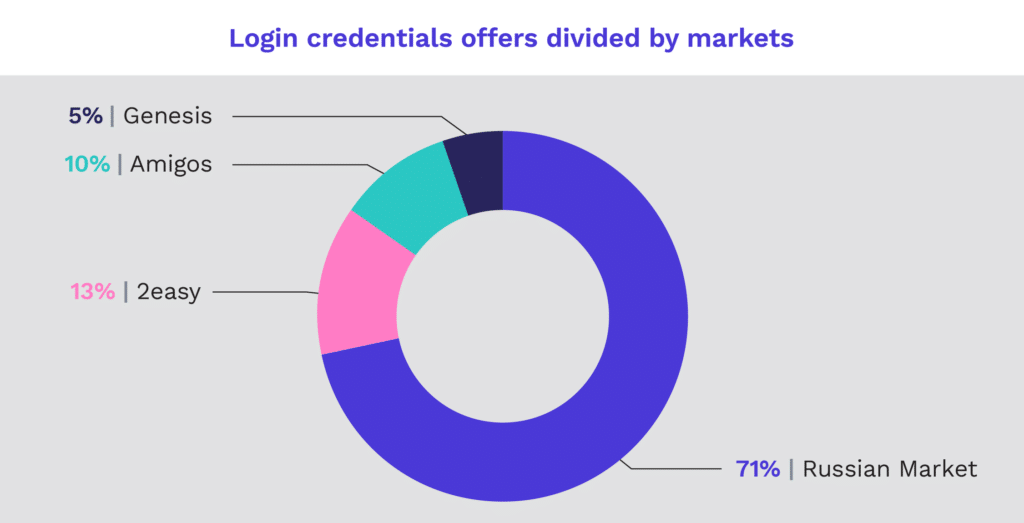
The sale of credentials on botnet markets affects individuals and businesses all over the world. We found that telecom, banking, energy, and government sectors were heavily targeted by threat actors selling stolen credentials on these markets. Understanding this trend is a critical first step for organizations seeking to protect their assets.
Bot markets, which have increased in popularity due to their ease of use and affordability, have created new risks for the enterprise market, requiring SOC teams to shift their focus outside of their organizations. Credential leakages pose a major threat to both a company’s internal resilience and reputation among customers, who make consumer choices based on data security.
SOC teams face the challenge of resource management when examining outside threats. There are numerous bot marketplaces, and SOC teams are unable to monitor them all, thus they must prioritize threat detection based on urgency and importance. Cyber Threat Intelligence (CTI) solutions can help SOC teams identify and focus on the botnet markets that pose the highest threat to their specific industry, country, or other parameters to maximize mitigation efforts and uncover the most stolen records.
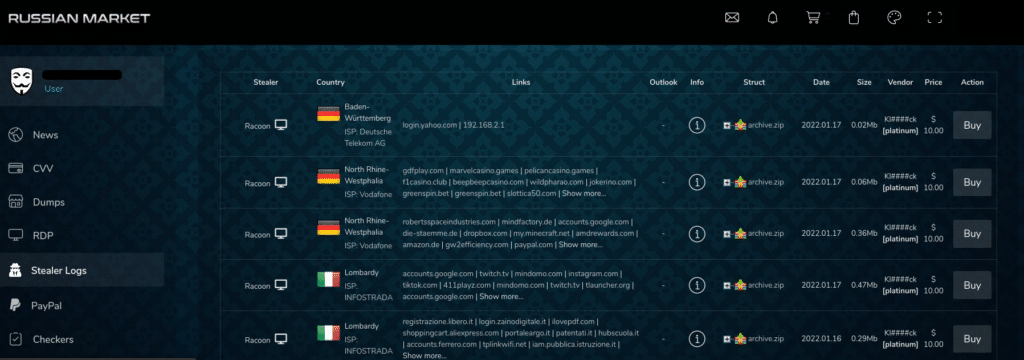
What are infostealers?
An infostealer, or information stealer, is malicious software that aims to gather information, such as usernames and passwords, from a system. Infostealers are often sold on hacking forums for prices ranging from a few dollars to hundreds of dollars for permanent use or for a subscription.
Infostealers are affordable hacking tools that enable those with no hacking skills to acquire credentials for just a few dollars. These tools have increased the number and variety of threat actors that buy and sell stolen credentials, creating heightened exposure for organizations.
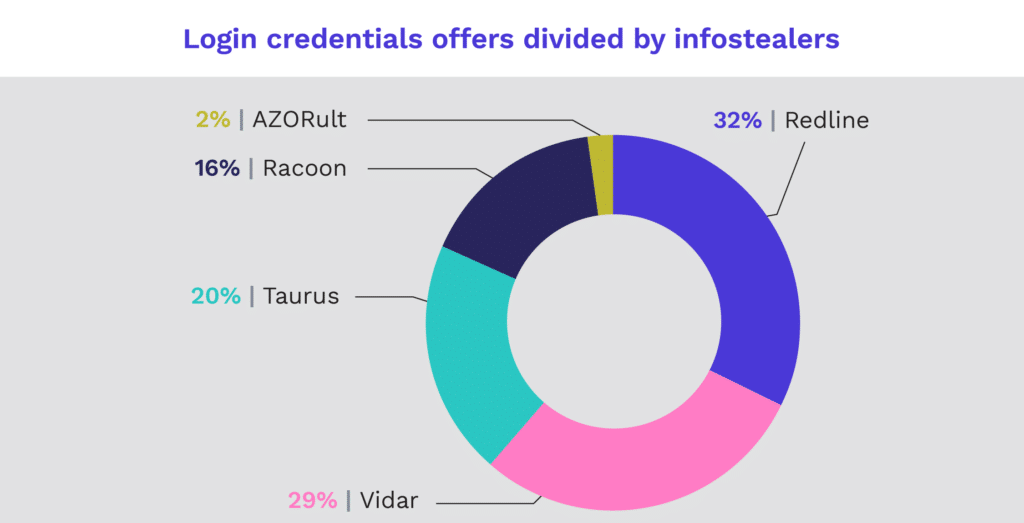
While bot markets use multiple kinds of infostealers, our research focuses on the top five: Vidar, Racoon, AZORult, Taurus, and Redline, which was the most prominent infostealer on botnet markets in 2021. Redline Stealer is actively developed and continually improved with widespread deployment using multiple distribution methods.
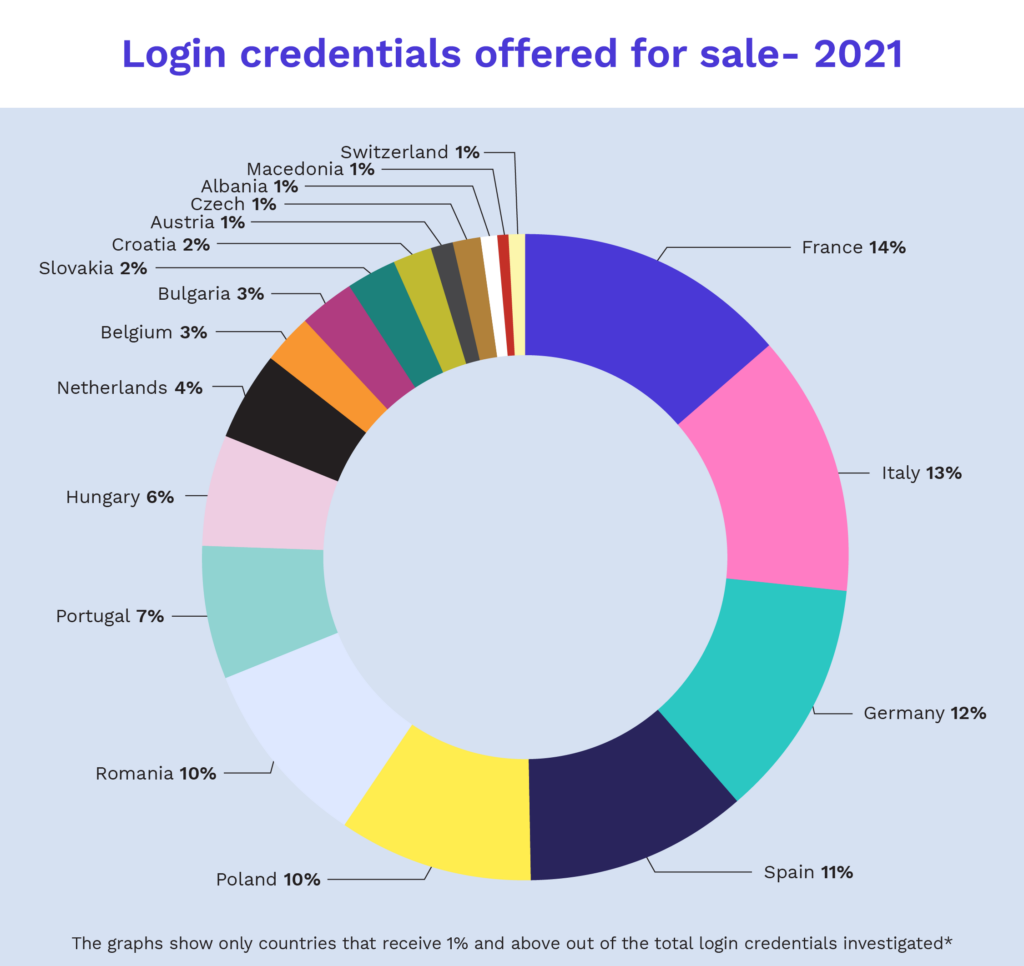
Botnet market statistics in 2021 by country and sector
Cognyte’s botnet market research deep dives into 20 countries, the majority of which are located in Europe, and four industry sectors: banking, telecommunication, government, and energy, to understand which countries and sectors are the most exposed in botnet markets worldwide. The data collection process focused on the top five banks, three major energy suppliers, three major telecom suppliers and the government top level domains (TLDs) in each selected country.

According to Cognyte’s findings, France was the most exposed country in these markets during 2021, while Italy was the most exposed country in 2020. The most exposed sector in 2021 was the telecom sector. It is worth mentioning in this context that Cognyte detected an overall increase in cybercrime and nation-state activities against the telecommunications sector.
Interestingly, during 2021, the country that was most exposed in the banking sector was Spain.
This data shows several conclusions:
- The telecom industry is likely the most exposed sector because companies in this sector hold vast amounts of personal customer data. The industry is thus putting a greater emphasis on cyber resilience.
- Larger countries in the EU are targeted more often since attacks on organizations in these countries are more likely to yield more credentials.
- Multi-national corporations, such as finance and telecom, are typically based in larger countries but serve many smaller countries, making them a prime target, especially as compared to local organizations in small countries.
How can you protect your assets against infostealers?
We believe the trend of botnet markets will increase in the coming years and will be the source of many future breaches. It is important to be aware of this threat and to be familiar with the mitigation methods to protect your organization or your private computer. For organizations, a CTI solution has become a must.
A CTI solution will enable several key elements necessary for an organization to protect its credentials and mitigate vulnerabilities:
- Source coverage: Examine the Deep and Dark Web to find new bot marketplaces as they emerge
- Attack surface: Monitor your specific organization’s assets, domain, c-level executives, IP ranges and more to ensure relevant and tailored intelligence
- Context & use cases: Reduce alert fatigue and act faster with contextualized analysis that accommodates specific business needs, cyber threats, and more.
- Mitigate threats: Mitigate and remediate threats through integrations, alerts, and playbooks so SOC teams can act on intelligence.
Learn more by reading the full Rise of Dark Web Botnet Marketplaces annual report.