Must-have insights on today’s most prominent threat actors
To beat the enemy, we need to know thy enemy.
The battle against cyber attackers is becoming more complex and more challenging every day.
There are many threat actors and they are using more sophisticated tools, technologies, and techniques all the time.
Therefore, if we want to develop a solid strategy for bolstering an organization’s security standing, we need to understand the landscape of threat actors:
- Who is the biggest threat, i.e. what type of actor is most active?
- What is their preferred approach, i.e. which vulnerabilities do they most frequently target?
- Where is the actor most active, i.e. countries and industries?
The need for practical insights
We understand how difficult it can be for security professionals to keep on top of all the data on all the threat actors out there, and extract meaningful insights so that they can take the right actions to mitigate risk.
This is why, together with Thales, we performed a comprehensive research on the most prominent threat actors operating in the world today, carefully analyzing:
- 490 attack campaigns
- 66 attack groups
- 525 attack tools
- 173 MITRE techniques
- 98 CVEs
The parameters we examined include:
- Associated malware campaigns, attack vectors, and TTPs
- Most-used exploits and CVEs
- Motivation and objectives (nation-state, cybercrime, hacktivism, cyber-terrorism)
- Targeted sectors and geographical areas
In this post we provide the key findings of this research.
These insights will enable you to better understand how the activities of the most prominent threat actors are relevant to you and what is the actual level of risk they pose to your organization.
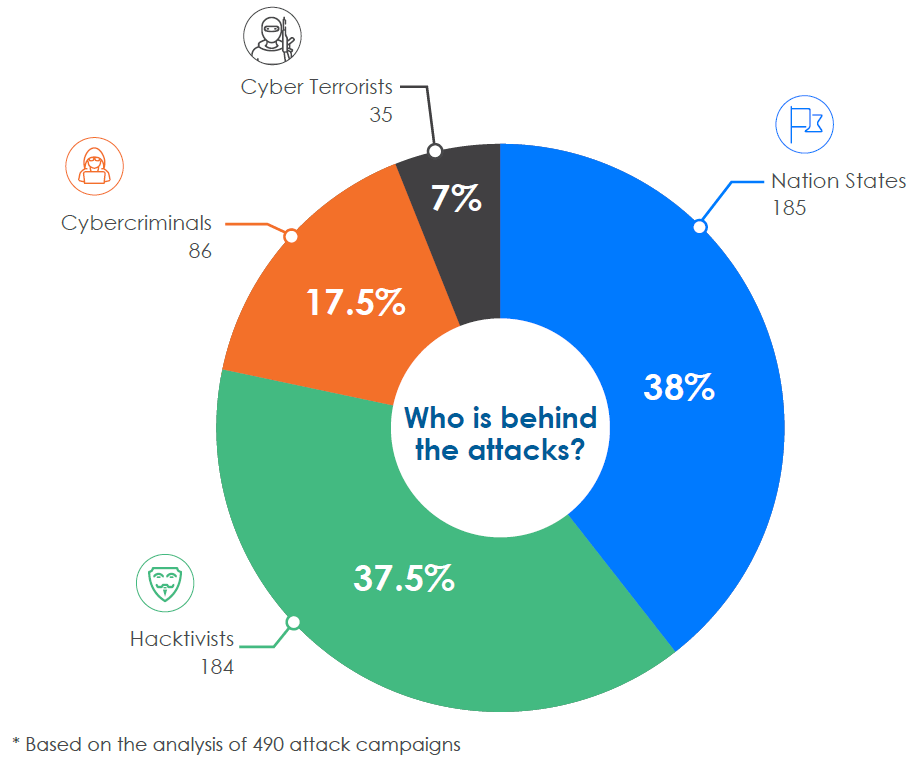
Who’s the biggest threat?
As we can see from the graph that the vast majority of attacks are launched by nation-states and hacktivists, with the former coming in at number one, and the latter at number two.
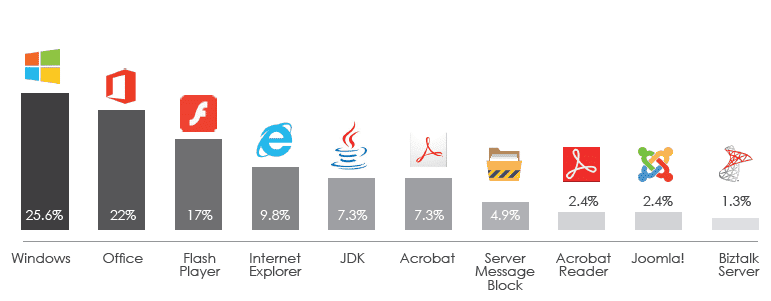
The greatest vulnerabilities
It may not come as a big surprise that Windows is the most vulnerable system, with Office the most vulnerable software suite, where the two represent the biggest vulnerabilities that require attention.
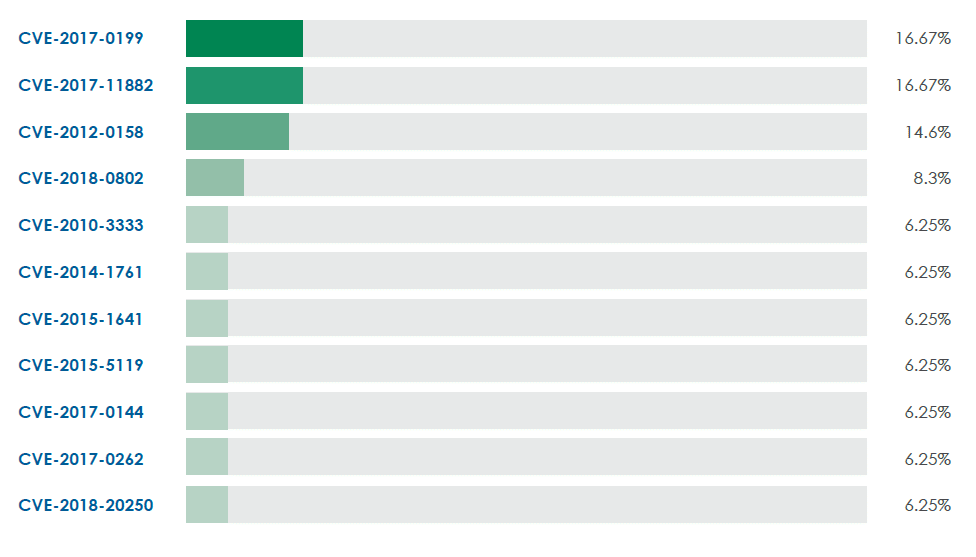
The most exploited CVEs
We know how difficult it is to update systems, even the most critical ones. But, when we procrastinate, threat actors don’t hesitate to capture the opportunity.
As we can see from the below table, the top three vulnerabilities for patching are CVE-2017-0199 (Windows and Office related), CVE-2017-11882 (also Windows and Office), and CVE-2012-0158 (Windows).
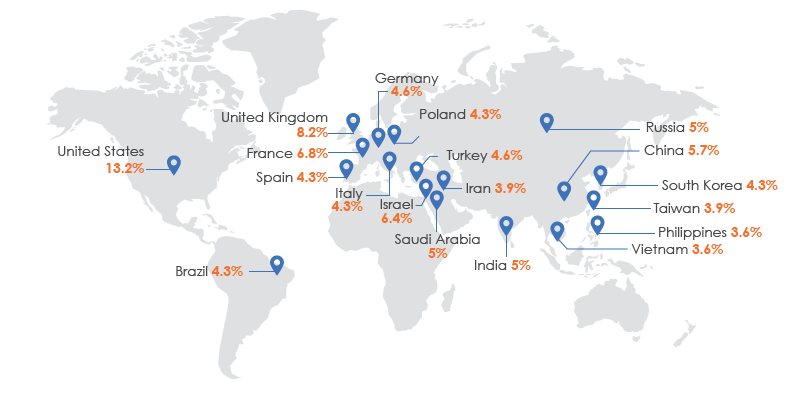
Which countries and industries are at highest risk?
The following map indicates which countries are on top of threat actors’ list, with the US coming in at number one.
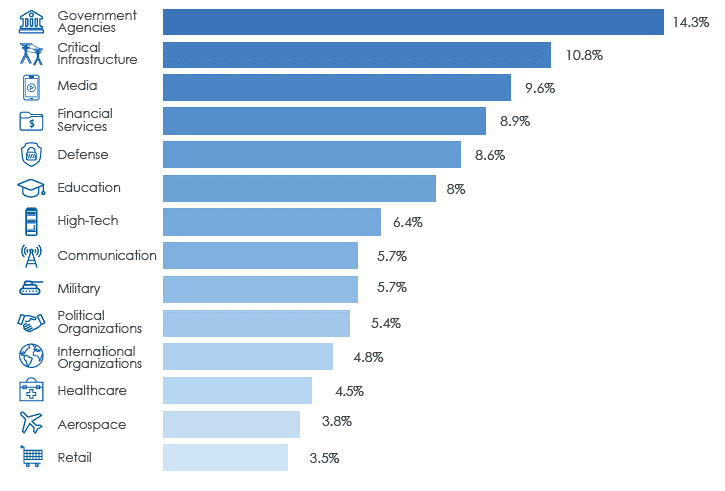
And the following demonstrates which industries are targeted most, with government, critical infrastructure, and media being the top three.
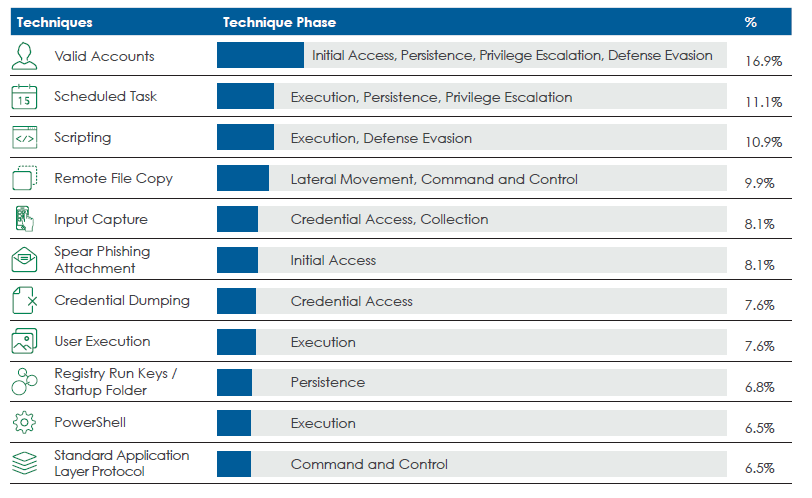
Top used techniques, based on the MITRE ATT&CK framework
Finally, the top techniques we should be on the lookout for are valid accounts, scheduled task, and scripting.
In conclusion
The importance of comprehensive threat intelligence to the efficacy of the cybersecurity organization cannot be understated. This requires performing threat actor profiling and clustering, threat hunting, and threat and risk scoping.
We also recommend maintaining a single knowledge base that contains a contextualized analysis of all the major parameters and distinctions. This includes the motives and objectives, targets, modes of operation, and technical skills of threat actors.
Maintaining this go-to resource for insights which contains not only data but context, is profoundly valuable for increasing resilience.
In addition to having the right information, having the right tools is also critical.
Cognyte offers threat intelligence analytics solutions which empower security operations center (SOC) teams with actionable insights in order to detect and mitigate cyber threats effectively.
To learn more about how you can connect the dots to identify, neutralize, and prevent the attacks of the most prominent threat actors, we invite you to contact us.
Author: Cognyte Cyber Threat Intelligence Research Group
Cognyte’s Cyber Threat Intelligence (CTI) research group is comprised of handpicked expert analysts with years of experience in security analytics. The team monitors, analyzes, and validates malicious activities on platforms such as social networks, mobile applications, deep web sites, dark web marketplaces, hacker forums, and more. They regularly produce threat alerts and insight reports based on region, industry, and organization-specific threats, with in-depth analysis and actionable recommendations. This way organizations can proactively identify and mitigate threats before they materialize, enhance their resilience, and prevent future attacks.