Prevent Advanced Cyber Attacks with Data-Driven Analytics and Automated Investigations
Get Multi-Level Visibility to Identify Threats
Collect and ingest petabyte-scale data, from sensors spread across organizational and backbone networks
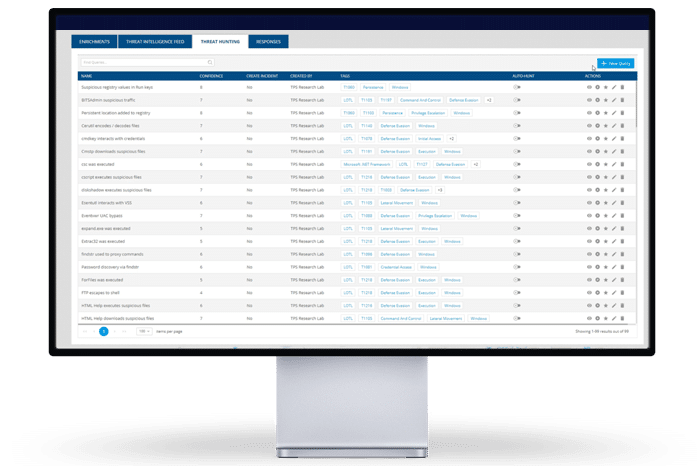
Hunt & Investigate Threats Automatically
Shorten investigation time with analytics-driven threat hunting and automated investigation tools
Increase Cyber Resilience with AI Algorithms
Run out-of the-box or self-developed analytics algorithms to reveal and prevent potential threats
How Advanced Analytics
Enable National-level Threat Hunting
Peta-scale Collection FROM ORGANIZATIONAL & BACKBONE NETWORKS
- Dedicated sensors gather logs from multiple monitored entities and from sources such as ISPs and CSPs
- All data is ingested into a national data lake to facilitate investigations and enable extended retention
- Data is transformed into a single data format and enriched for data science activities and advanced analytics
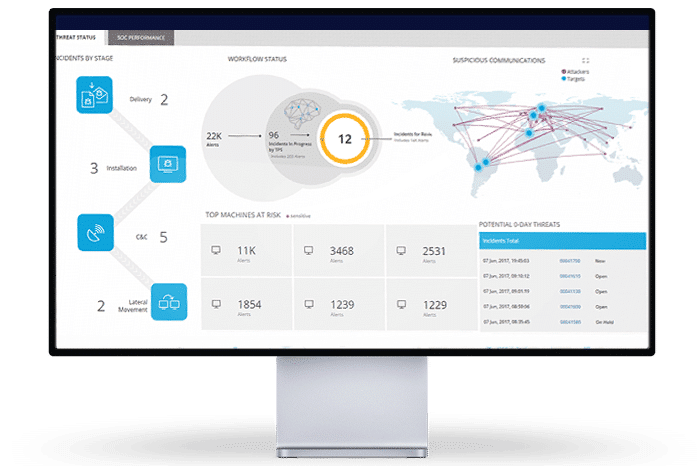
INVESTIGATION ENVIRONMENT & DEDICATED THREAT HUNTING TOOLS
- Analyst-oriented interface enables investigators to discover anomalies by querying multiple parameters and wide datasets
- Leads are enriched with contextual data from threat intelligence sources, IP geo-location, and tags
- Big Data forensics & AI algorithms fuse OS processes, files, and registry events for a complete attack storyline
- Cyber profiles are generated for entities such as IPs, endpoints, servers, files, processes and monitored sectors
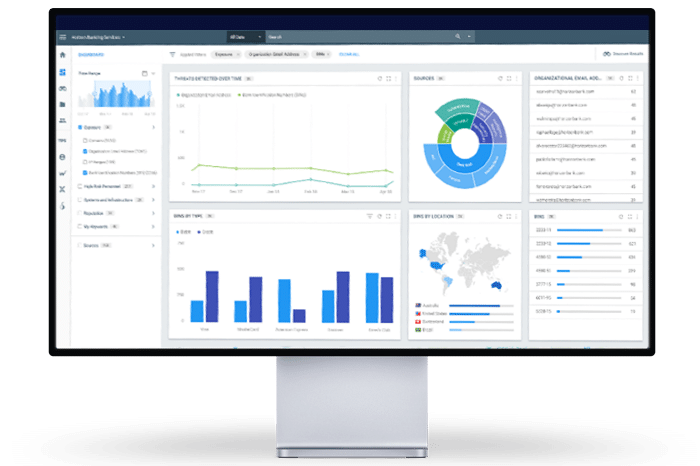
Built-in Cyber Analytics
- Analysis of defined sequences, as well as mathematical, statistical, and ML models, reveals potentially malicious activities
- 100s of analytics covering MITRE ATT&CK techniques, advanced attacks and malwares examine incoming data to identify anomalies
- Dedicated Integrated Development Environment enables to develop analytics based on deployment, threat landscape & use case
register to our monthly newsletter
More results...