Discover Malicious Cyber Activity at its Earliest Stages
Gain Visibility Beyond Your Organization
Understand where potential attackers are active, which tools they use, and what they are planning
Identify & Prioritize Threats
Convert raw data into context-based, enriched, Actionable Intelligence for proactive cyber defense
Build Proactive Cyber Defense
Strengthen resilience by integrating threat intelligence findings into your existing cybersecurity environment
How a CTI Platform
Leads to Proactive Defense
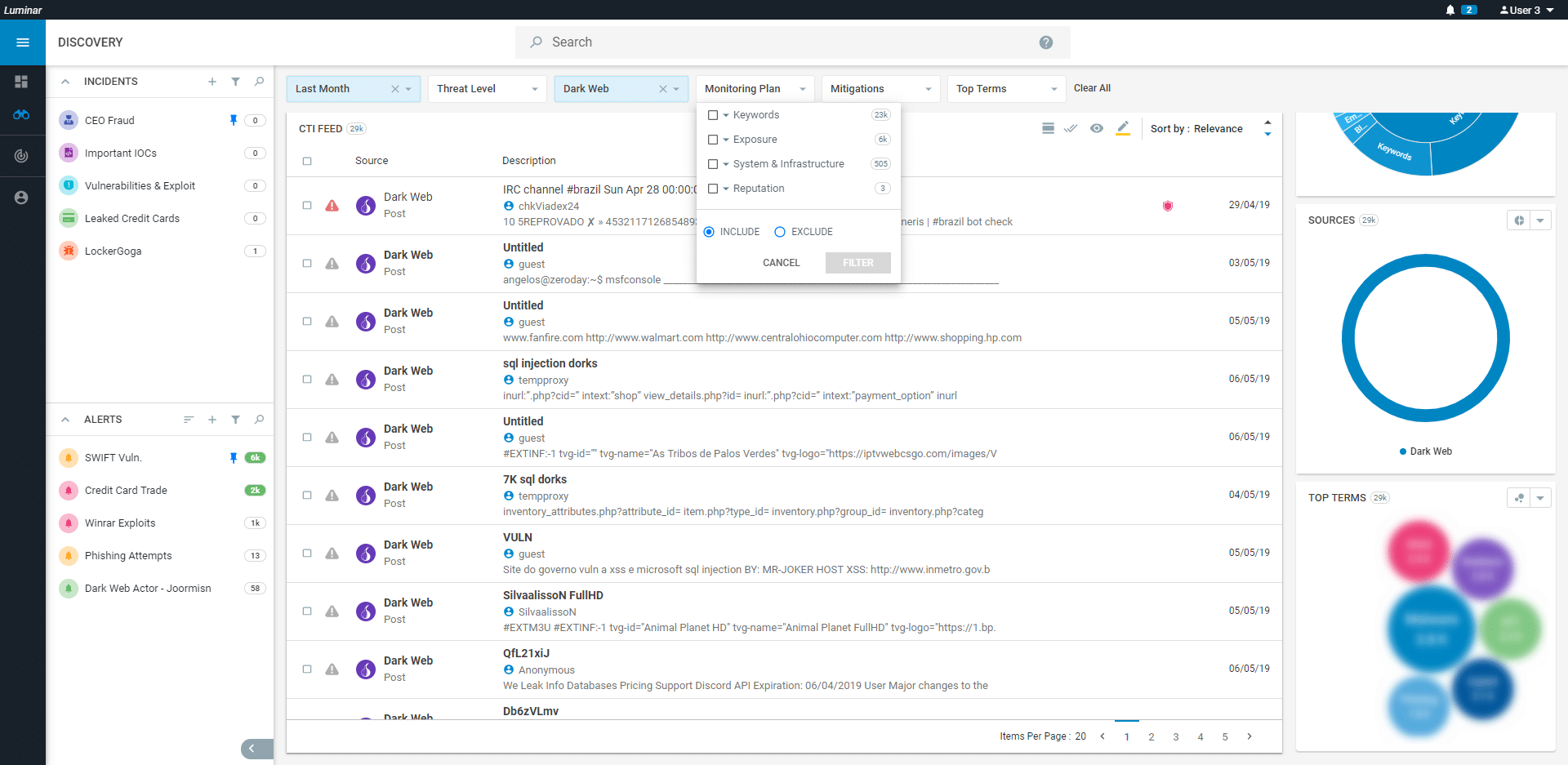
EXTENSIVE COVERAGE for TARGETED DATA FUSION
- Automatically harvests data based on the organization’s predefined threat hunting requirements
- Monitors threats on open, Deep and Dark web sites, as well as closed forums and messaging platforms
- Continuously updates “live” monitoring based on keywords, specific personnel, assets, and other customer-defined feeds

CONTEXTUAL PRIORITIZATION ANALYTICS
- Cross-referenced to a threat intelligence repository and classified by industry, topic, attack group, and more
- CTI platform outputs cover 20+ languages in numerous domains, such as financial crime, cyber-terrorism, and nation-state
- Constant flow of technical analysis validated with IOCs to improve detection of malware
- Analytics-driven insights to classify and prioritize threats based on customer
pre-defined needs
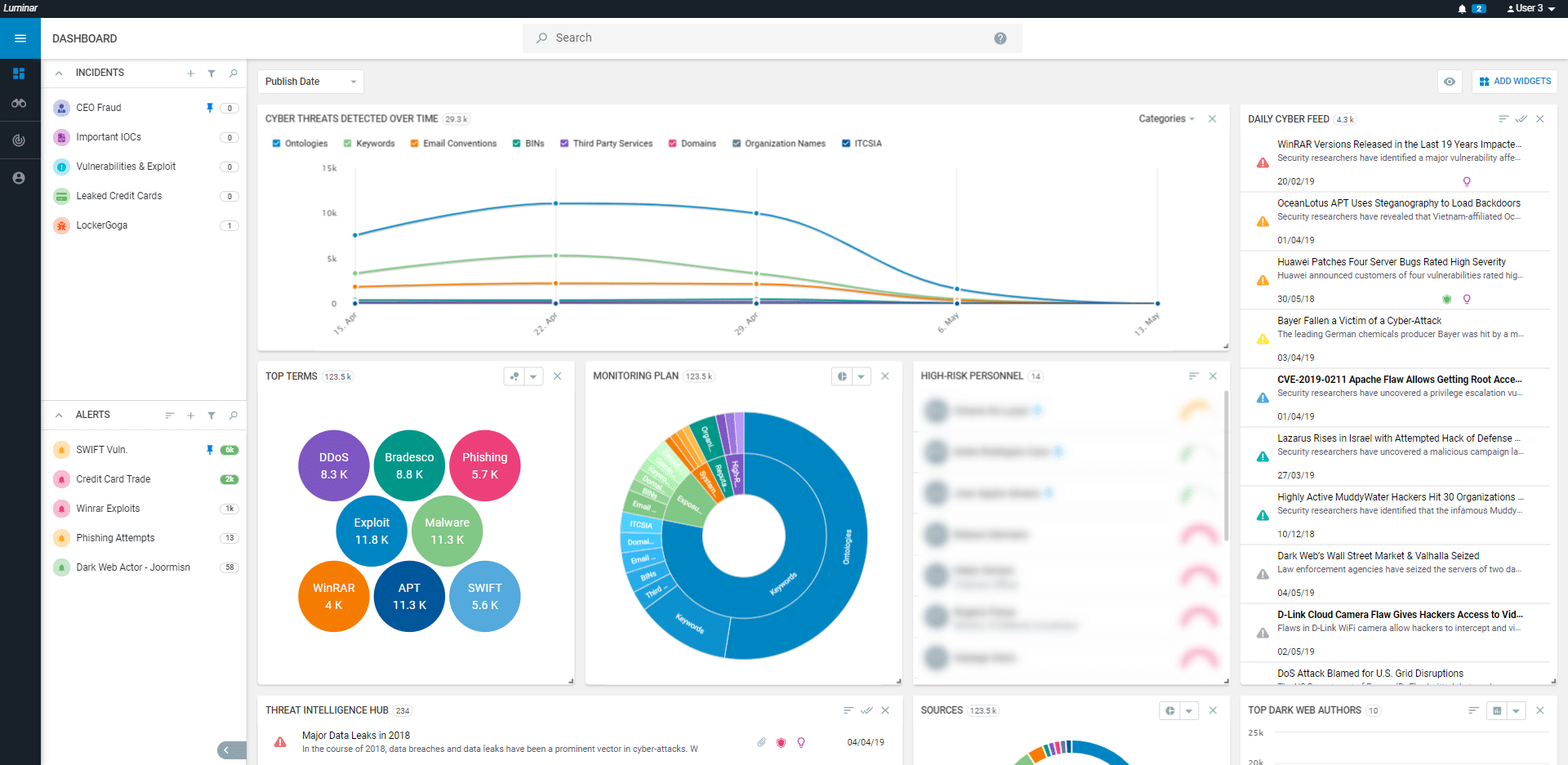
AUGMENTED ECOSYSTEM DEFENSE & RISK MITIGATION
- Customized real-time dashboards provide access to human-enriched analytics & customer-tailored insights
- Automated 24/7 monitoring covers full threat life cycle with a window to attackers’ identities, motives, and methods
- Leverages existing security ecosystem with automated updates to strengthen the security environment
Learn More
register to our monthly newsletter
More results...


