What you need to know about the top 4 global ransomware vulnerabilities and how to stay protected
We understand how critical it is to stay on top of the most prominent ransomware attacks, to accurately understand the threat, and the best way to stay protected.
That’s why our research group set out to investigate just that.
As a result of their investigation, they uncovered the top four types of attacks that have been active in recent months – and which are expected to continue into 2021.
The top targets
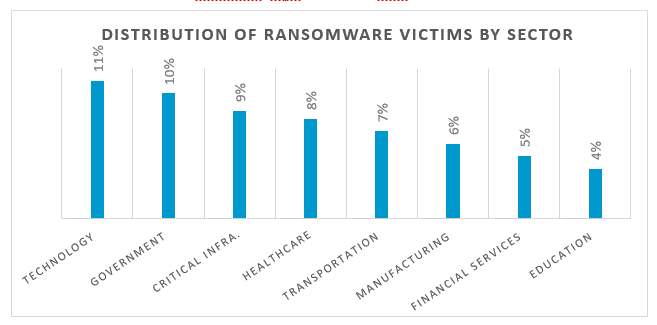
But first, a word about the targets. After examining approximately 180 different incidents, the group identified that the most targeted sectors are:
- Technology at 11%
- Government at 10%
- Critical Infrastructure at 8.6%
Additional high target sectors include healthcare and pharmaceutical (8%), transportation (7%), manufacturing (6%), financial services (5%) and education (4%).
As for the most active ransomware strains, these are:
- Sodinokibi/REvil
- Maze
- Ryuk
What do they all have in common?
The most interesting and important takeaway from this investigation is that all of these attacks had exploited one or more of the same four vulnerabilities.
In order of most to least exploited, these are:
- CVE-2019-19781
- CVE-2019-11510
- CVE-2012-0158
- CVE-2018-8453
Let’s take a closer look.
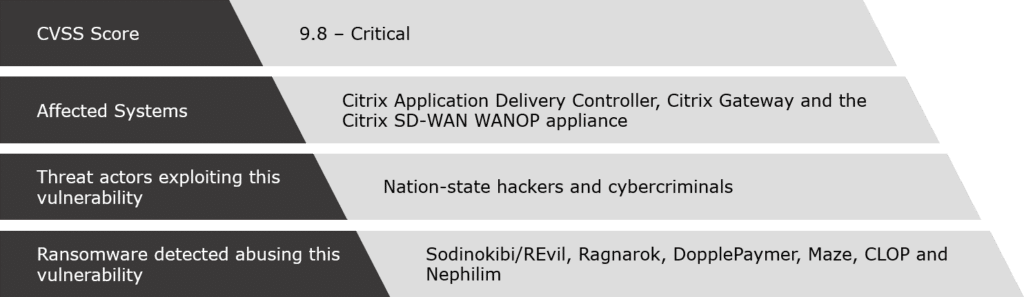
CVE-2019-19781
The what
The CVE-2019-19781 vulnerability affects remote access appliances manufactured by Citrix, primarily the Citrix Application Delivery Controller (ADC), formerly known as NetScaler ADC.
The how
When successful, exploiting this vulnerability enables the attacker to connect remotely and execute arbitrary code on the affected computer.
The who
Unfortunately, CVE-2019-19781 was successfully exploited by many threat actors, including:
- The REvil gang against the Gedia Automotive Group (January 2020)
- The Ragnarok ransomware gang, which downloaded scripts and scanned targeted systems for computers that had the EternalBlue vulnerability (January 2020)
- The DopplePaymer gang against Bretagne Telecom (February 2020)
- The MAZE ransomware gang against cyber insurer Chubb (March 2020)
- The CLOP ransomware gang against Indian conglomerate, Indiabulls, which used the Citrix NetScaler ADC VPN Gateway (June 2020)
- The MAZE ransomware gang again, this time against IT services giant, Conduent, which had a Citrix server that was neither patched nor properly updated (June 2020)
Moreover, the New Zealand CERT had also reported that many threat actors are leveraging this vulnerability and that the Nephilim ransomware gang may have also attempted to exploit it.
CVE-2019-11510

The what
CVE-2019-11510 affects VPN Pulse Secure products.
It enables attackers to:
- Remotely access targeted networks
- Remove multi-factor authentication protections
- Access logs that contain cached passwords in plain text
The how
CVE-2019-11510 has been repeatedly and successfully exploited in multiple ransomware attacks.
Among the techniques used was:
- First, the attackers gain domain admin privileges.
- Then, they use an open-source remote access software (VNC), to perform lateral movement on the targeted network.
- Thereafter, they turn off the security software and infect the system with the REvil ransomware.
The who
Three notable examples of a CVE-2019-11510 exploitation include:
- As noted, the REvil ransomware gang, which paralyzed the systems of Travelex for several weeks, after the company didn’t patch its VPN.
- Nation-state threat actors against the IT systems of several hospitals and government entities in the US.
- The Black Kingdom ransomware gang against several targets.
CVE-2012-0158

The what
Although CVE-2012-0158 is an old vulnerability in Microsoft products, it is still one of the most exploited.
In fact, it has a long history of being repeatedly and successfully exploited by some of the most sophisticated groups operating in the world today.
The how
CVE-2012-0158 enables attackers to remotely execute code on the victim’s computer through a specially crafted website, Office, or .rtf document.
A relatively new method that threat actors are now also using is to leverage the Covid-19 theme. We especially noted this in cases against Canadian medical and academic organizations.
The who
Examples of ransomware that have attacked this vulnerability include:
- The EDA2 ransomware, a strain of a wider ransomware family known as HiddenTear. This was used in a phishing attack involving emails that appeared to be coming from legitimate World Health Organization addresses. These emails contained malicious files that remotely executed code to infect recipients.
- A ransomware dubbed RASOM also launched a similar phishing campaign.
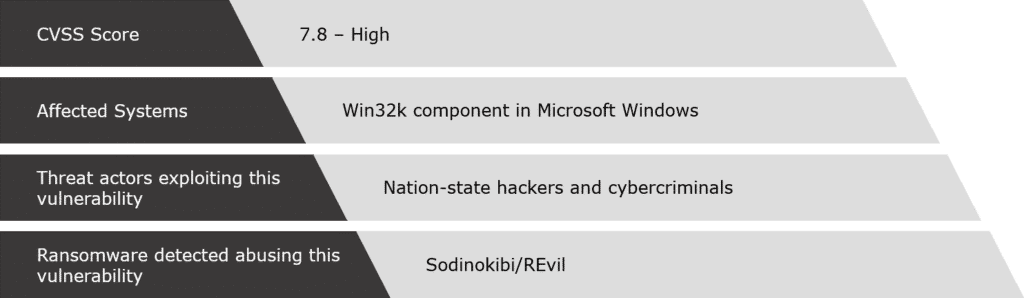
CVE-2018-8453
The what
CVE-2018-8453 resides in the win32k.sys file in Windows, which fails to properly handle objects in memory.
The how
A successful exploitation of this vulnerability enables attackers to:
- Run arbitrary code in kernel mode
- Install programs
- View, change, or delete data
- Or create new accounts with full user right
The who
The main threat actor in exploiting this vulnerability is the Sodinokibi/REvil ransomware gang. This group launched multiple attacks in 2019, in Taiwan, Hong Kong, and South Korea.
In July 2020, the gang was back, but this time it attacked the Brazilian-based utility, Light S.A.
In this case, the attackers demanded a ransom at the equivalent of $12.3 million. Once the deadline for paying the ransom had passed, the ransom even doubled.
Key takeaways on prevention
While the first vulnerability we discussed was publicly disclosed at the end of December 2019 and fixed a month later – the threat was present for many months (and is still with us).
Similarly, with the second one – although it was public for some time and even patched in April 2020, many organizations have yet to execute this patch. Consequently, they remain exposed as the threat continues.
Accordingly, we cannot underestimate how important it is to ensure timely patching and security update installations.
This is the best defense against vulnerabilities and your best chance at minimizing the risk of ransomware.
We understand that it’s not easy. Often resources are limited, there are many legacy systems that are difficult to protect, and patch implementation can be time consuming.
However, when vulnerabilities are left unpatched, the damage can be too great.
To learn more about how you can connect the dots to identify, neutralize, and prevent attacks, read about Cognyte’s threat intelligence analytics solutions here.