2024 Threat Intelligence Report
The past year has brought unprecedented advancements in the realm of threat intelligence — chief among them being the emergence of generative AI (GenAI), which has the potential to reshape the threat intelligence domain across the board, from the way that threat data is processed, to the way that cyber threats are understood and mitigated. Over the course of the last year, Cognyte’s LUMINAR Threat Intelligence Research Group leveraged GenAI to analyze 1,128 global security incidents covering organizations in 26 key industries, in addition to having visibility into 6 million sales ads of stolen access credentials published on black marketplaces, and 100+ ransomware Dark Web extortion sites, with the key findings available in Cognyte’s 2024 Threat Landscape Report. The cyber incidents analyzed targeted companies and organizations in 26 key industries.
Read on to learn about the key findings from Cognyte’s 2024 Threat Landscape Report.
Key Findings
- More than 40% of attacks documented targeted technology or governmental entities.
- 50% of attacks were financially-motivated, with ransomware attacks by attack groups considered a top threat vector.
- The MOVEit flaw (CVE-2023-34362) was the most abused vulnerability by attack groups in 2023.
- Ransomware continues to be a top concern for organizations. Multiple new ransomware variants emerged in 2023, including two, Rhysida and Akira, which were among the top 10 active ransomware groups in 2023.
- Well-known info-stealers (Redline, Racoon, Vidar) dominate the stolen access credentials threat vector (responsible for ~85% of infections).

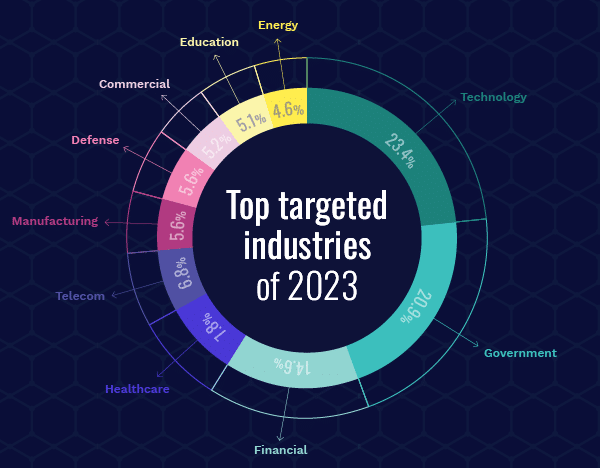
Top Targeted Industries
The top 5 targeted industries remained consistent throughout both 2022 and 2023. One explanation for this trend is that government and technology organizations are common targets for nation-state threat actors that seek to exfiltrate sensitive data. The financial industry, on the other hand, is a popular target for cybercriminals interested in financial profit, and healthcare organizations are targeted for their sensitive data. The healthcare industry is known for its gaps in security and therefore considered to be a “soft” target with high success rates for attacks.
The following are the top targeted industries for cybercrime in 2023 (percentage across overall incidents analyzed):
- Technology (23.4%)
- Government (20.9%)
- Financial (14.6%)
- Healthcare (7.8%)
- Telecom (6.8%)
- Manufacturing (5.6%)
- Defense (5.6%)
- Commercial (5.2%)
- Education (5.1%)
- Energy (4.6%)
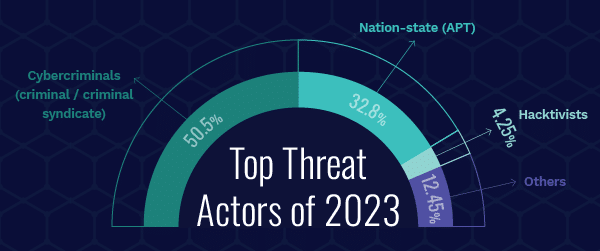
Top Threat Actors
Cybercriminals, primarily motivated by financial gain, remained the leading threat actors in 2023, aligning with the steady increase in financially-motivated ransomware attacks globally.
The following are the top categories of threat actors worldwide in 2023 (percentage across overall incidents analyzed):
- Cybercriminals (criminal/criminal syndicate) (50.5 %)
- Nation-state (APT) (32.8%)
- Hacktivists (4.25%)
- Others (12.45%)
Read on to learn about the top threat vectors of the past year.
Most Exploited CVEs
Abusing vulnerabilities is a popular attack vector that poses a major threat to organizations, allowing threat actors to quickly gain unauthorized access and potentially cause extensive damage. It is crucial for organizations to regularly update software and products to mitigate these risks. The presence of zero-day flaws, which are exploited by threat actors before the flaws are discovered, underscores the importance of promptly patching vulnerabilities to prevent mass exploitation by threat actors.
The following are the top most exploited CVEs of 2023 (percentage across overall incidents analyzed):
- MOVEit flaw – CVE-2023-34362 (28.5%)
- WinRAR flaw – CVE-2023-38831 (21.4%)
- Citrix Bleed – CVE-2023-4966 (16.7%)
- Zoho’s ManageEngine ServiceDesk flaw – CVE-2022-47966 (11.9%)
- 0-day in GoAnywhere MFT – CVE-2023-0669 (11.9%)
- Barracuda Email Security Gateway flaw – CVE-2023-2868 (9.6%)
Top Ransomware Groups
The ransomware threat is escalating, posing a major danger to organizations worldwide and causing substantial harm. In 2023, ransomware attacks surged by nearly 40%, indicating a significant rise in malicious activities. The actual number of attacks is likely much higher than reported figures, highlighting the widespread nature of the threat. Ransomware as a service (RaaS) is a key driver of these attacks, enabling threat actors to provide ransomware platforms to affiliates for financial gain.
Most ransomware groups employ extortion leak sites to pressure victims into paying ransoms, threatening to leak stolen data if demands are not met. Ransomware attacks typically involve gaining access to a system, encrypting files and demanding payment from victims. RaaS groups employ various tactics, techniques, and procedures (TTPs), making each attack unique based on the affiliate conducting it. Double extortion tactics are common, where attackers steal files, and then encrypt victims’ systems and threaten to leak them unless the ransom is paid.
Emerging ransomware groups are making a significant impact – Two new ransomware groups, Akira and Rhysida, are among the top 10 active ransomware groups, despite having emerged very recently. In 2023, several ransomware groups ceased their operations altogether or had significant changes, such as rebranding. 2024 is expected to witness additional ransomware attacks by Akira and Rhysida, if they are not stopped by authorities.
The following is a list of the top 10 active ransomware groups of 2023:
- LockBit
- Cl0p
- Alphv
- BlackCat
- BlackBasta
- Play
- Vice Society
- BianLian
- 8base
- Akira
Stolen Access Credentials
Stolen access credentials, including login information and financial details, are traded on Dark Web marketplaces. These stolen credentials are often obtained through malware infections known as info-stealers, which are designed to steal credentials and other sensitive data, allowing attackers to launch various cyber attacks, including data theft, ransomware, BEC (Business Email Compromise) scams and cyber espionage, once they gain network access. The threat from info-stealers is expected to rise in 2024, with new malware emerging alongside established threats, and we expect to see an increase in the use of novel malware for log stealing.
The following is a list of the top emerging info-stealers of 2023:
- Lumma
- RisePro
- StealC
Looking Towards the Future
2023 marked the rise of GenAI, starting with the emergence of ChatGPT and leading to a widespread adoption of GenAI across technology sectors. GenAI is being integrated into threat intelligence, offering the capability to process, contextualize, and enrich data for a deeper understanding of threats and proactive mitigation strategies. This integration is poised to revolutionize threat intelligence in 2024, providing organizations with a crucial advantage in combating evolving threats.
To keep pace with the rapid development of new, more sophisticated threats, it is essential that threat intelligence analysts and SOC teams enhance their risk assessment and data analysis capabilities to effectively counter these threats.
GenAI technologies can support threat intelligence use cases such as:
- Contextualizing and enriching threat data
- Identifying and visualizing key security trends
- Sorting and filtering raw data
- Prioritizing threats
- Creating reports
How the LUMINAR Threat Intelligence Solution Can Help
LUMINAR is an analytics-driven external threat intelligence solution, enabling security and risk management leaders to maintain visibility of their threat landscape and extract timely, accurate and actionable insights that can be applied before, during and after threats reach the organization. LUMINAR addresses the increasing demand to know more, prioritize better, and act faster in accordance with the threat landscape and organizational risk.
Click here to access the full 2024 Threat Landscape report to gain in-depth insights and learn how to protect your organization.