Blog
-

2022 Government
CIO Survey Shows
Key Big Data
Challenges and PrioritiesAs investigation teams in government and security organizations face increased struggles in the big data era, Chief Information Officers (CIOs) must equip their organizations with more powerful tools to conduct investigations, assess risks and mitigate threats. CIOs play a critical role in building the right technology infrastructure and strategy across the organization to ensure that…
-

How Digital Intelligence Platforms Accelerate Investigations
Digital intelligence platforms, often called investigative analytics platforms, have become increasingly popular among law enforcement and security organizations in recent years. Due to the rise of digital technologies and the explosion of big data, traditional investigation methodologies have become far too labor-intensive to keep up with the amount and diversity of data sources. The siloed…
-

The War in Ukraine: from Fake News to Cyber-Attacks
Conventional warfare has not been a high priority for many countries for the better part of a century, and intelligence and military organizations have become focused on threats such as terrorism and serious crime. The current situation in Ukraine, one in which a global power has invaded another sovereign state, has delivered a wakeup call…
-

Botnet Marketplace Statistics in 2021
Botnet markets have been evolving and growing since they first emerged in 2018. These automated stores sell stolen login credentials for websites and platforms, obtained from computers infected with an infostealer, to cyber criminals. Some markets provide a full system of fingerprints to threat actors so they can mask themselves as victims. Cognyte’s latest annual…
-

Digital Wallet Cybercrime is the Next Target to Watch
Rising interest of threat actors in digital wallets may have affected trade of stolen credit cards on dark web markets The use of digital wallets is on the rise and is likely to continue to grow and supplant credit cards as the payment method of choice for online purchases. Since the start of the Covid-19…
-
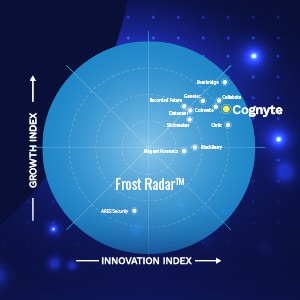
Cognyte Named Leader in Digital Intelligence Solutions by Frost & Sullivan
Security organizations are in a perpetual race to keep up with evolving digital technologies and the rise of big data. Technology continues to provide criminals with sophisticated tools to commit crimes and evade law enforcement. At the same time, the increased volume, variety, and complexity of data has made it difficult for organizations to generate…
-

Join us at ISS World Middle East 2022
Cognyte is headed to Dubai to meet with law enforcement homeland security professionals, security analysts, investigators, cyber-crime pros, and more at the world’s largest law enforcement and public safety gathering. We are excited to meet in person with the security community to exchange ideas, share best practices, and discuss the latest developments in security analytics….
-
IBM sells i2: what’s next for your analytics platform?
IBM’s sale of i2 to Harris makes the security community rethink what they need in an investigative analytics platform The world of security analytics is a buzz concerning the recent sale of IBM’s i2 portfolio to Harris Computer. Users have become speculative as to potential shifts and the uncertainty of the solution’s roadmap and ongoing support. Savvy organizations are using this as an opportunity to evaluate what they need in…
-

Are Telecoms the Most Popular Target of Cyber-Attacks in 2021?
Recent headlines have focused on data breaches of social media platforms, but the frequency and impact of these attacks pale in comparison to those in cyber-criminals’ favorite industry: telecommunications. Cyber-attacks on telecoms are popular because their databases carry detailed information on millions of customers. A successful telecom data breach could yield contact details, social security…
-

5 Reasons Why Criminals & Terrorists Turn to Cryptocurrencies
In this blog, Cognyte presents the appeal of cryptocurrency to criminals and terrorists, outlines the challenges facing security and law enforcement, and explains how Cognyte’s solution can help overcome these challenges and track down those behind illicit crypto transactions.
More results...